So have you taken our advice from our post on completing a Password Checkup? If so, I bet you're feeling better about your security. We are proud of your efforts! Cybercriminals will need centuries to crack your passphrase(s). Sadly, these criminals have another tool up their sleeves that is more effective and requires less time and effort...
91% of Successful Data Breaches Start with Spear Phishing
It seems ridiculous, I know, but according to KnowB4.com, 91% of successful data breaches are a result of a specialized attack known as "spear phishing." In case you are not familiar with this topic, we want to bring you up to speed. Check out this 3 minute video to get an idea of what phishing is in general.
Did you find yourself wondering if you have ever fallen victim to a phishing scam? Perhaps you know someone who gave away sensitive information to a phishing attack. Either way, the threat is real, and the only way to avoid it is to learn more about it.
Social engineering sounds fancy. It might even sound benign or perhaps even like a good thing. Social engineering is essentially synonymous with phishing. The main goal of social engineering (and phishing) is to get you to give up sensitive information. They are so successful because attackers know how to make it more likely you will make a mistake.
You are probably very familiar with the part of the brain called the amygdala. This part of the brain is associated with emotion. It is often called upon in serious survival situations. When it is activated, it makes it harder for the critical thinking portion of the brain (the prefrontal cortex) to override the decision-making process.
Can you wager a guess as to what part of your brain a hacker is looking to activate? Correct! Your amygdala! They do this by trying to trigger your fear or anger emotions. Add in a layer of surprise, and you're significantly more likely to make a mistake and click a link, or reply to the message. The results can be disastrous.
Learn from the Professionals
Take it From a Professional Con Artist
Perhaps you have seen or at least heard of the film Catch Me if You Can. In this short video, you'll learn how to spot the red flags and techniques often employed by today's modern con artists (social engineers).
How did you feel after watching that video? Leave us a comment at the bottom of this post.
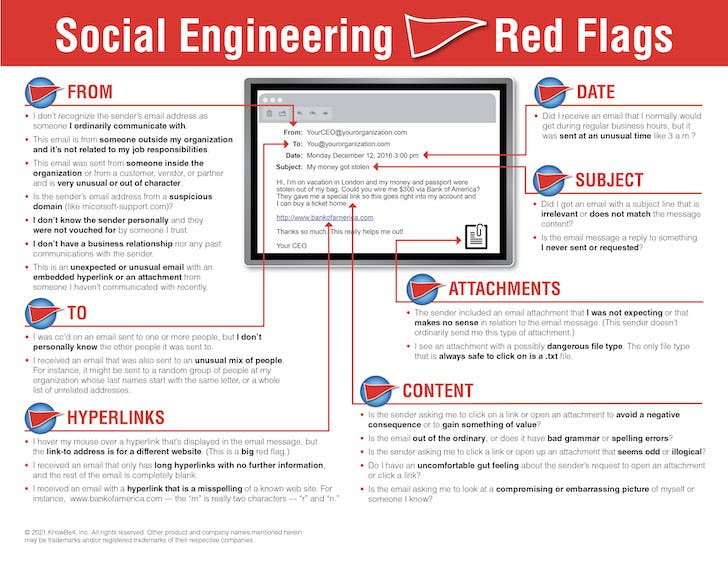
Where Can You Find the Red Flags in a Phishing Email?
Take a moment to look over all the ways an email could/should stand out as suspicious before you click, forward, or reply. You can see that there are many ways that a cybercriminal can make mistakes and give us clear signs to be suspicious. Some of these mistakes can be obvious while others may be less obvious. We'd love to hear from you in the comments if you have any stories about ways you detected a phishing email.
See a Larger Image
Regular phishing attacks tend to follow a "spray and pray" approach. The attackers blast out emails to as many recipients as possible in the hopes that someone falls for the attack.
How is Spear Phishing Different?
As the name suggests, this type of attack is more sophisticated and targeted. Rather than "phishing with nets", spear phishing takes more effort on the part of the attack to select and target a specific group or even a single person. The attackers will have to "do their research" to construct a campaign that is more likely to succeed. Often times this involves researching the organization using sites like LinkedIn.
Being Phished is Just the Beginning
Giving out your personal or sensitive information is goal #1 for cybercriminals. Once someone given out their sensitive information, the bad guys move to working on their next phase. The details of what they do after someone has been phished are not critical for us to understand at this time. What is critical is that we alert an administrator that you or a colleague has been a victim of a cyberattack.
It's natural to be embarrassed or feel ashamed of falling victim to a cyberattack like this. We can't let this stop us from reporting the incident, however.
As If It Wasn't Bad Enough Already
There are 2 more terms I want to introduce before we end this post:
- Vishing
- Smishing
I know. At this point, the terms are just absurd, right? Vishing is something we are all used to. It seems that (for me at least) I receive spam calls daily -- sometimes multiple times a day. Here's some irony for you. I just received a spam call while writing this paragraph. I am not making this up. While many of the spam voice calls we receive are scams, they may or may not be vishing. Rather than looking for you to buy a product, vishing campaigns are again looking for you to divulge sensitive information that they can then use at a later time.
So What Exactly Is Smishing?
I have to admit, this one almost got me. Smishing involves SMS or text messages. More likely than not, the messages sent to you will contain a link. This link can lead to several things, but I will share my own "close call."
If you are like me, and you are a Prime member, receiving packages is a common occurrence. Sometimes packages don't arrive when they say they will. I have received text messages before regarding packages and delays. Fortunately, I wasn't expecting any deliveries at that time so the message seemed immediately suspicious. The link in the text message almost certainly would take you to a page that looks exactly like an Amazon sign-in page. If you were still unsuspecting, at this point would enter your login credentials and they would have access to your account.
For this reason, it is wise for you to make use of 2 factor authentication. What's 2 factor authentication? I'm glad you asked, that will be the topic of next cybersecurity post.
I congratulate you for making it all the way through this post. I know it may have been stressful for you or maybe even brought back uncomfortable memories. Being aware of how we ourselves can be the "weak links" in the security armor is extremely important.
Please remember that your EdTech specialists are always happy to help you. Head on over to our contact page if you want help with tech including help with cybersecurity. If you have any thoughts on what you've read in this post, we would love to hear from you below in the comments. Until next time, stay safe!
Did you miss our first post?
Read our first post on saving passwords.



Social Engineering